Introduction:
When you are PenTesting an iOS application, you would want to read the code of the provided application and understand the backend classes and hidden information. Using this, you can try and exploit the application to gain access to sensitive information or to redirect the flow of the application in an malicious manner.
Reverse Engineering an
iOS application is completely different as compared to an Android
apk. The complete original source code cannot be revivied from an
existing iOS application. Only, declarations for the classes,
categories and protocols can be decompiled from an given application.
Requirements:
- iOS device must be jailbroken.
- OpenSSH should be installed on the iOS device.
- SSH Client on your machine.
- "Class Dump" should be installed on the iOS device via "Cydia"
Detailed
Steps:
Step
1: SSH in to your iOS device using credentials as root:alpine.

Step
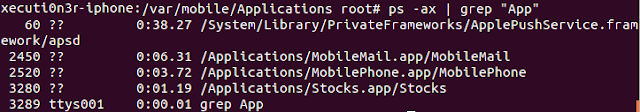
2: Launch the application on your device and note down the
application location on your device using the "ps -ax |
grep "App"" command.

As shown in the above
diagram, the application is running from location “
/Applications/Stocks.app/Stocks”
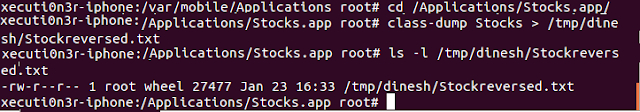
Step 3: Navigate to
that location “/Applications/Stocks.app/” via the shell.
We will use “Class
dump” to reverse engineer this application. It is a command-line
utility for examining the Objective-C runtime information stored in
Mach-O files. It generates declarations for the classes, categories
and protocols. We will do
this using the command
class-dump Stocks >
/tmp/dinesh/Stockreversed.txt
As
shown in the below screenshot, the application was decompiled
properly and the header and implementation files are copied to
location /tmp/dinesh/
in the file Stockreversed.txt

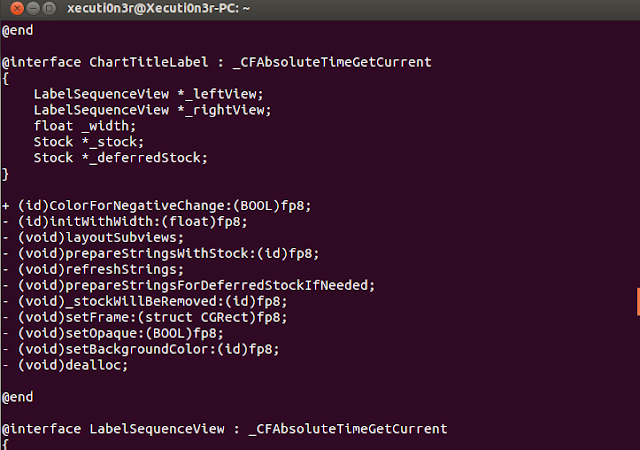
Below screenshot shows
the contents of the file “Stockreversed.txt” is clearly readable
and all kinds of hidden secrets and logical flaws can be understood
from here.

The above screenshot
shows that the source code is in cleartext and can be easily
analysed.
Now that you have the declarations of the classes and the protocols you can go ahead an debug the application using GDB or, hook on to the functions present in the application via MobileSubstrate and try to change its behavior.
However, many a times this process is not so straight forward and the developers put in additional security feature to prevent the attackers from reversing the applications by using debugging techniques. The ways by which, we can bypass this restrictions and try and dump the class declarations in an encrypted iOS application would be explained in the next blog post.
References:
To dump the class information using Class-dump is it really required to have a jailbroken device and carry out the process on it?
ReplyDeleteWill it not be sufficient if we have the ipa file and class-dump-z on a machine?
Hi Anonymous,
ReplyDeleteUsing classdump on your jailbroken device is not compulsary. You can pull the ipa file from the device and run classdumpz on your local machine also. It would yield the same result.
On running class-dump on non- jailbroken deivce it shows following error.
Deleteclass-dump: Input file (appName xxxxxxipa) is neither a Mach-O file nor a fat archive.
Thanks, worked perfectly.
ReplyDeleteDo we have any emulator for testing iOS application?
ReplyDeleteI am getting errors saying the file is not a Mach-O file nor a fat archive. Any idea why?
ReplyDeleteI figured it out... Class-dump does not support 64-bit Mach-O files... And I am on an iPad mini 3 and most apps are 64-bit.
DeleteNice blog, thanks for sharing this informative ideas and i read the whole information and you have done marvelous job and i bookmark this information for future use.
ReplyDeleteiOS App Development Company
If are facing problem to install any third party apps on your ios device, use this software to do it hassle free.
ReplyDeleteHappymod is a new generation App Store for Modified Apps and Games that generate premium features. By Installing Apps and Games from HappyMod, users can get more coins, paid features and premium subscriptions for free.
ReplyDeleteThank you very for share us such kind of good info. I love your blog
ReplyDeleteemail address lookup
Great content material and great layout. Your website deserves all of the positive feedback it’s been getting. 192.168.l.254 is a private IP address that comes in a range booked from IANA (Internet Assigned Number Authority) for specific purposes, though in many cases users mistype the IP address as 192.168.1.254 where the character one is assumed as letter L.
ReplyDeleteThis comment has been removed by the author.
ReplyDelete